
Challenges and Solutions in the German Power Grid
Achieving end-to-end cyber security
Over 60% of electricity generation in Germany comes from renewable energies, which reached 100 gigawatts (GWp) for the first time, distributed across ~ 5 million solar installations. The base load amounts to 40-50 GW. The challenge of the energy transition: Increase to over 90% and balance volatility while maintaining high security and resilience.
Critical Conditions Expected in the Power Grid
Critical conditions in the electricity grid are already expected this year on weekends with low loads and plenty of sunshine. Switching off rooftop PV is becoming increasingly important for the grid. The the remaining government with CDU/FDP agreed.
Heat pumps and air conditioning systems (HVAC), wallboxes for electric vehicles (including bidirectional charging) and battery storage systems (BESS) can also be connected and controlled remotely. The aggregation of hundreds to millions of individual devices and systems creates a virtual power plant that can flexibly provide up to several gigawatts of power. As Internet of Things (IoT) devices, the decentralized generators and consumers are increasingly open on the Internet and communicate with their manufacturers' cloud systems. For monitoring, but also for over-the-air firmware updates.
Securing these process chains is crucial for the cyber resilience of our future energy system and cyber security against potential attacks. An end-to-end view of security is essential here.
BSI-Supported Security Architecture
In recent years, the Federal Office for Information Security has designed an IT security infrastructure based on Common Criteria for cyber security, which has now been rolled out in cooperation with the Federal Ministry of Economics (BMWK), the Federal Network Agency and various expert committees.
Providers such as Arvato Systems offer an end-to-end secure solution for this in accordance with the guidelines of the German Federal Office for Information Security (BSI). The basis is the so-called Smart Meter Public Key Infrastructure (SM-PKI), which uses asymmetric cryptography for communication between different market partners and devices. This ensures that different IT systems can be securely controlled right up to the controllable resources in the building.
These end-to-end processes were tested by the BMWK-funded research project "SecProMo", a consortium around smartOptimo, Items, Osnabrück University of Applied Sciences, Stadtwerke Bielfeld, PPC and Arvato Systems.
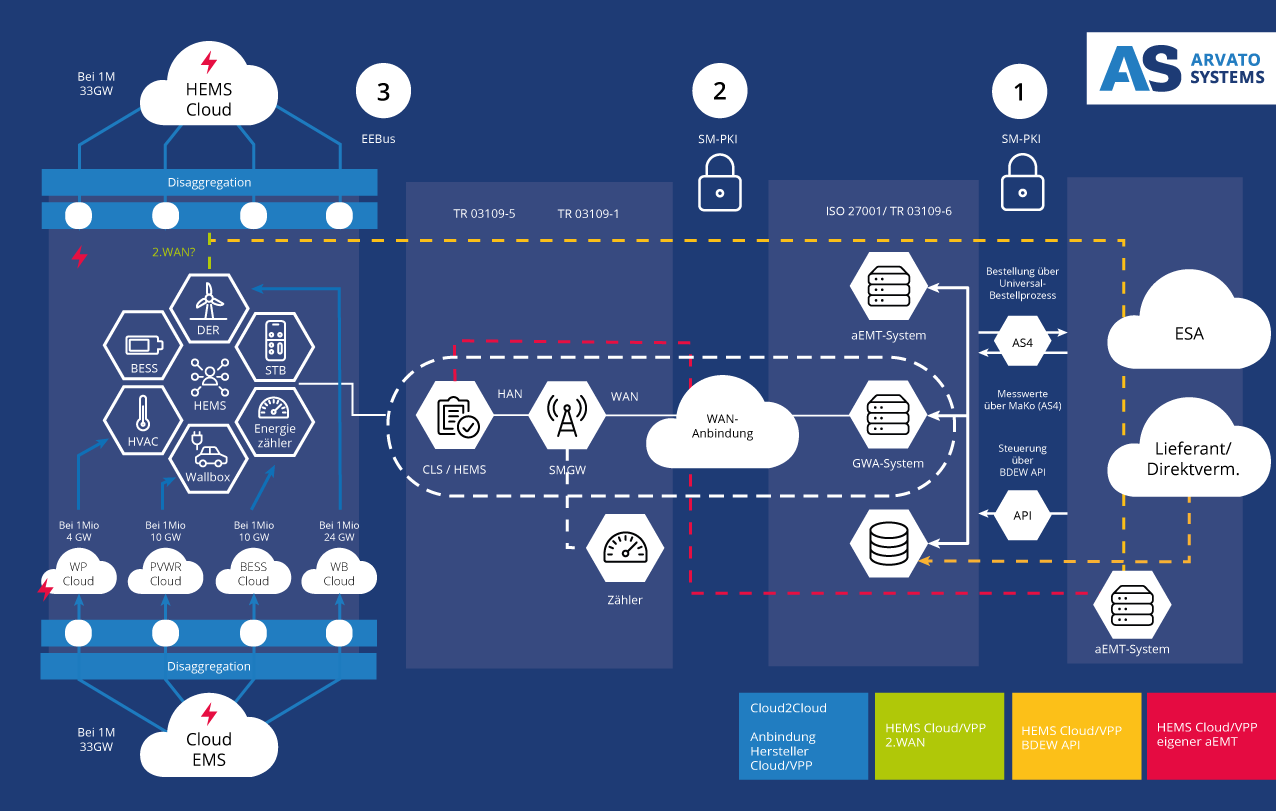
In order to connect direct marketers, electricity suppliers and energy service providers to the IT systems of the metering point operator (MSB), which rolls out the metering and control technology, AS4 market communication and API web services are crucial for the future of market communication (see illustration). These technologies improve communication between the players in the German energy market. For example, the highly secure and highly scalable cloud technology from Arvato Systems is used. The use of hardware security modules ensures the highest security standards.
In the next step, control commands are transmitted by the gateway administrator or control box administrator via secure communication to the IoT devices, the smart meter gateways and the control boxes behind them.
From there, the technical resources are controlled or their power consumption and output behavior is influenced. The communication between the devices within a building, the so-called technical resources, and the coordination of their use is also crystallizing as a standardization of communication. There is a standardization partnership between EEBus e.V. and the German Federal Office for Information Security (BSI). Asymmetric cryptography is also used here, and devices of all kinds, be they wallboxes, energy storage systems or heat pumps, can be integrated into a control system via the EEBus protocol.
This allows the system operator, for example the electricity supplier and direct marketer, to control and regulate the building and its consumers and generators via a secure communication link via the smart meter gateway. On the other hand, a standardized communication interface is offered to the grid operator via the API web services. In the event of a grid bottleneck, the grid operator can send a specific control command to the system or grid connection via its low-voltage cockpit or congestion management. In future, the grid operator will transfer a maximum target power value, which should be at least 4.2 kW per appliance, for example, to the Home Energy Management System (HEMS) at the virtual grid connection point. This HEMS optimizes the energy flows in the building within these framework parameters. This ensures that even in the event of corresponding PV generation, this is used first for self-consumption.
Battery storage systems, wall boxes and heat pumps can be integrated and controlled in a targeted manner. Buildings as decentralized cells are first optimized locally, which contributes to the resilience of the system in terms of both electrical engineering and safety. This is in contrast to other approaches being pursued internationally, in which the control of controllable consumers such as heat pumps or wallboxes is mapped via a central cloud platform and a connected virtual power plant. Here, hundreds of thousands to millions of controllable consumers are stored and aggregated centrally in a data platform of the appliance manufacturer. This has the advantage that they can be managed centrally as a virtual power plant and traded on the electricity market (EPEX). In this way, flexibility can be offered for balancing energy as well as on the intraday and continuous intraday market. So-called aggregators are required, which often coincide with the role of the direct marketer.
IT Security Assessment of the Connection
In times of trade wars and hacker attacks, protecting our energy infrastructure is crucial. The primary task of the IT architecture of our energy system is to ensure cyber resilience and cyber security.
In order to rule out manipulation by attackers and ensure the resilience of the system, it is important to compare the different mechanisms of the two approaches to controlling decentralized systems and evaluate them in terms of cyber resilience.
It can be seen that there is a significantly larger number of attack vectors in the case of central cloud infrastructures. As can be seen in Figure 1, various infrastructures can be attacked:
- The individual IoT devices, which in this variant all communicate openly with the internet from the building. The flexibility provided here is usually between 2 and 10 kW, which can be called up.
- The cloud platform for, for example, a device type such as wallboxes, inverters and heat pumps from the respective manufacturer, which aggregates measurement data from the IoT devices and enables control and over-the-air updates (blue arrows in Figure 1, Cloud2Cloud connection variant).
The available power is already in the gigawatt range with millions of installed devices (especially PV inverters). - The aggregator or virtual power plant, which links the various manufacturer clouds and thus gains access to a large number of systems and therefore also to a great deal of controllable flexibility or power, offers a potential attack surface.
With several million decentralized controllable systems in the German power grid, outputs of several gigawatts are expected. This means that the aggregating system and all resulting communication steps must be classified as system-critical and fall under IT baseline protection.
For example, "generation plants" and "control/bundling of electrical power" already fall under KRITIS from a capacity of 104 MW.
The three leading inverter manufacturers are from China. Safety requirements and sovereignty of the control of the systems require special checks and standards, as these are not directly within our control.
This contrasts with the connection of technical resources in the building exclusively via the secure infrastructure shown in the diagram. The standardized BDEW API web services can either be used for grid-serving control by a grid operator or for market-serving control as an active external market participant. Firmware updates etc. could also be securely transmitted to the devices in this way.
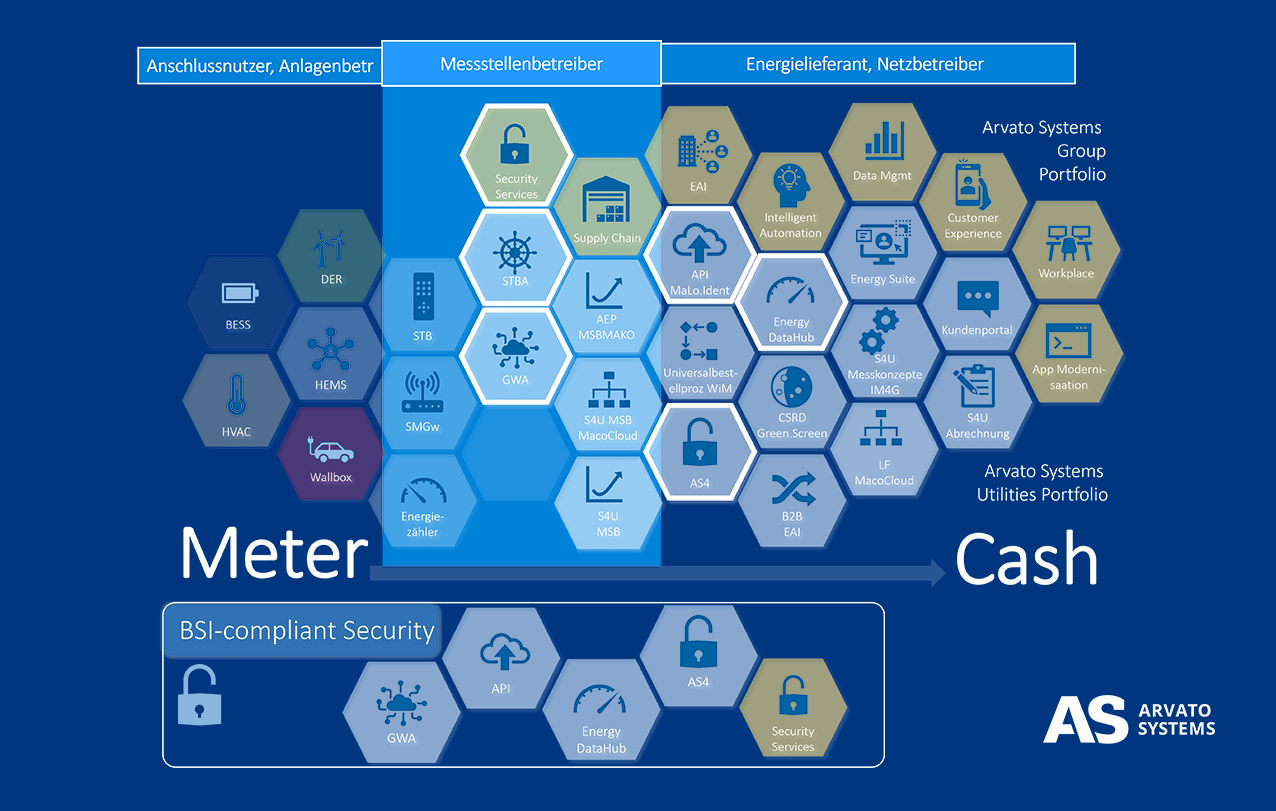
Arvato Systems has particular expertise in the field of security infrastructures for regulated areas. This is of interest to old and new players in the energy supply sector through a wide range of best-practice security services and is now supplemented by energy-specific applications along the entire Meter2Cash process.
Our Energy System Is Changing
The combination of dynamic tariffs and control of decentralized resources is becoming essential. Due to increasing decentralization, dealing with IoT and cyber security is becoming more and more central. Securing the process chains is crucial for the cyber resilience of our future energy system and security against potential attacks. An end-to-end view of security is essential here in order to continue to guarantee a high level of supply security.
Written by

André Hoffmann is the Head of Product Portfolio Energy at Arvato Systems and an IT expert for the energy and utilities industry. He is responsible for developing platform solutions and driving innovation for solutions for smart meters, billing, market communication, customer service, and IoT.